Beyond Five Nines: Adding Value with Security Metrics
Employing a solid security system for business IT is imperative for reliable safety and overall good practice. Cybercriminals are nipping at the heels of businesses by looking for an open window, a crack in the foundation, or a naïve employee.
There are defined standards that provide guidance for information security, helping organizations govern the ways they track, measure, monitor, and react to security needs and issues. The methods of doing so have evolved over the years, prompting the need for new and modernized ways of looking at information security, giving regard to metrics rather than timing.
Setting the Standards
Also known as the ‘bureau of standards,’ the National Institute of Standards and Technology (NIST) sets guidelines and identifies ways of measurement for the science and industry sector. NIST sets out to promote innovation and competitiveness and defines its core cybersecurity framework as the following five functions: identify, protect, detect, respond, and recover (NIST Cybersecurity Framework). It uses these functions to promote key activities and business best practices, both with infrastructure requirements and with compliance.
NIST aims at data security – much the same focus as businesses everywhere. A recent study performed by Cisco explained that, “Cybersecurity is essential to digital success, with the potential to fuel an estimated $5.3 trillion in private sector Value at Stake over the next decade. Sixty-eight percent of this value is tied to firms’ ability to integrate cybersecurity into their digital foundation to drive innovation and growth.”
The Life of Five Nines
For over 30 years, the term ‘Five Nines’ (or 99.999%) has been used as a measure of downtime. It counts the time of system availability and divides that availability by the number of minutes within a specified period. Five Nines availability equates to 5.39 minutes within a year for planned or unplanned downtime. Techopedia explains, “five nines ensures high availability and reliability of a computer or service. It is often the desired percentage availability of a given system or service.”
Stemming from the telecommunications industry, Five Nines was created as a gage for reliability in providing phone services to customers. Over the years, questions have been raised regarding the accuracy of this method of IS measurement. With the focus on uptime and availability, Five Nines has a limited impact on and assessment of cybersecurity and system vulnerabilities. During an era of heightened attacks and seasoned attackers, although it may indicate security issues, it isn’t a security measure.
To achieve the approach of Five Nines, high availability must be made for various segments including network functionality, computing resources and infrastructure, applications and software, and the operational services of the physical data center. Measuring this operational seamlessness in providing IT services internally or externally raises questions that stem from using Five Nines as a metric. They include:
- From an IT operations perspective, are scheduled or emergency maintenance efforts included?
- With cloud and wide area networks (WAN) in place, are single site outages considered downtime?
- Is there concern with non-operational hours (such as a European data center supporting North American operations)? Are hours outside typical North American business hours considered within the Five Nines window?
- If a system or application is hosted by a third party, is daily maintenance or downtime caused by that third-party solution considered a disruption? What happens if the contract with the third-party provider is outside of the SLA pertaining to internal systems and supplying services? For example, critical, internal systems have an 8-hour recovery time, however a supplier only guarantees a 24-hour recovery for a critical system.
Adding Metrics Adds Value
The NIST Cybersecurity Framework model regards four areas of information security as the most important:
- Quantified and assessable measures
- Supporting data for those measures
- Implementation of repeatable processes
- Efficient and effective tracking system
Value-added metrics help to discern how security measures are functioning over a designated period. Usually reported quarterly, the results help to identify downtime and delays, and uncover points of vulnerability and complaints. These measures can then be used to apply techniques based on the measures gathered, to utilize resources and track performance to the betterment of the organization.
Cyber security teams need to focus on how they can add value rather than being viewed as an obstruction to the business and its employees. Value added metrics must be supported by data that clearly quantifies the measurement. Cybersecurity value added metrics include:
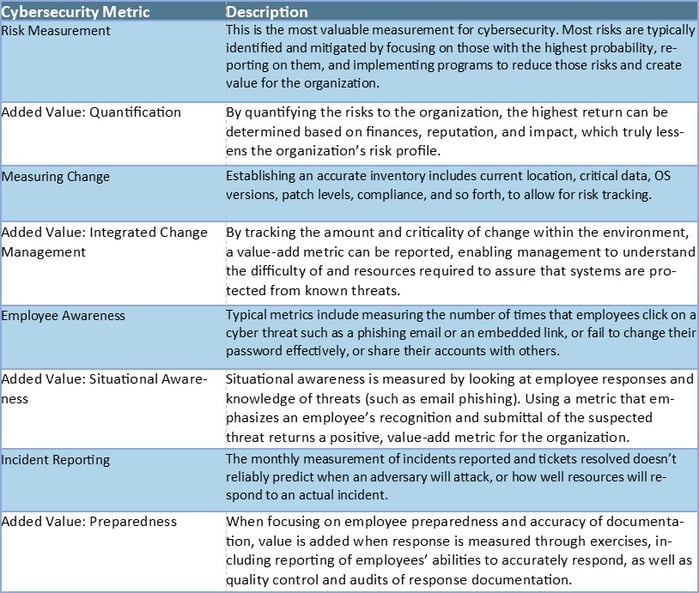
Deliverability is Vital
Today’s businesses need to be able to deliver on their IT components 24/7/365. Metrics that go beyond Five Nines encompass important security aspects including accuracy of data, and empowering cybersecurity to be enabling for the business.
Is your company utilizing best practice when it comes to its security measures and metrics? Are you considering going beyond the Five Nines approach, and enlisting better value-added efforts? Advancements in technology provide strong, viable solutions that help build and support reliable paths toward safety, functionality, and success.





